Dark web is an encrypted part of the Internet that is not available to the public in traditional search engines such as Google. The Dark Web, also known as the Dark Net, accounts for most of the illegal activities on the Internet. It may also be used for lawful reasons by legitimate users, such as those who want to protect the privacy of certain information, or those who want to participate in exclusive online clubs or social networks. This guide explains the dark web, from its origins and how it works to legal uses, risks, and the hidden dangers it presents. Understanding the dark web is critical for organizations to recognize and counter the threat posed by the dark web.
What is the Dark Web?
The dark web is the part of the internet that is not indexed by Google and Bing search engines. Compared to the surface web, dark web websites are inaccessible and cannot be searched normally because to access it one needs special software. These websites run with anonymity masking the identities of the users as well as site operators.
What is the Difference between Deep Web vs. Dark Web?
The terms “deep web” and “dark web” are often confused with each other. They are terms to call parts of the internet that regular search engines can’t reach. Still, they’re not the same thing. The deep web is just anything on the Internet that is not indexed by a search engine-that means everything from password-protected websites to private databases-even your personal email inbox. The dark web, however is just a small part of the deep web but fashioned specifically to maintain anonymity.


The Origins of the Dark Web
Originally, the dark web was designed as a means of anonymous communication. The U.S. government developed technologies in the 1990s with the purpose of allowing surfers to anonymously roam the Internet. There is the Tor Project, which covers the auspices under which most of the connections referred to as “this web” occur; this undertaking has been said to have been accepted by the government while proving itself to be a very effective tool for private, secure communication online, particularly in political and socially charged scenarios.
How Does the Dark Web Work?
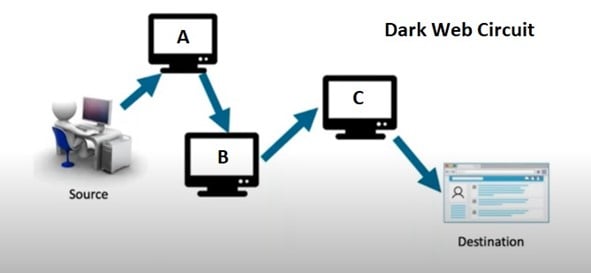

Role of Tor and Onion Routing
The most commonly used access point to dark web is through Tor browser that becomes “The Onion Router.” Tor uses onion routing technique to anonymize internet traffic. Each time you attempt to access a site on the dark web, your request passes through layers of encryption and multiple nodes. You can rwad more about “The Evolution of Biometric Authentication: From Fingerprints to Multi-Modal Security“.Each node strips one layer of encryption-this is why it is called “onion routing.” This is a very difficult thing for anyone to trace back to you.
Dark Web URLs
Domain names for dark web sites aren’t like those found on the regular net, with endings like .com or .net. Instead, they contain long, seemingly random URLs that end with .onion; for example, they are intended to be unpleasantly hard to recall and guess. Moreover, it is impossible to access these .onion addresses from standard browsers; a Tor is needed to open them
Anonymity and Privacy
Anonymity is one of the characteristic features that ensure that both website operators and users will not be identified through their use on the dark web. In many respects, anonymity provides privacy and shelter to vulnerable users, but in other respects, it also throws open the door to illegal activities, which is why dark web has gained such widespread notoriety.
The legal uses of the dark web
Even with all these evil deeds, the dark web is not used for illegal purposes only. In fact, many people and organizations use the this web for legitimate purposes, such as a means of privacy, freedom of expression, protection against oppressive governments, or simply to avoid surveillance by their own governments.
Whistleblowing and Journalism
Dark web Journalists and whistleblowers are able to anonymously and secretly communicate using this. Leak sites hosted on the this web allow uploading information to journalists with unknown identities, like the SecureDrop online leak site. This web has become a practical tool to reporters who cover politically sensitive or high-risk environments.
Freedom of Speech in Oppressive Regimes
It is a way by which citizens of countries with high internet monitoring and censorship activities get an easy access to information that is uncensored and the ability to communicate freely with anyone without any sorts of restrictions. Activists, political dissidents, as well as organizations that aim at human rights, find means and ways to use the dark web in an effort to avoid surveillance and persecution.
Personal Privacy
The dark web may be an avenue for some people to enhance personal privacy. In today’s scenario, and due to increased government surveillance and corporation data collection, this web is a circumvention tool for people who want to keep their online activities private. Most certainly, people who care about privacy will not venture into the dark web; however, using tools like Tor is common for anonymized browsing on the normal internet.
The Illegal Side of the Dark Web
Although the dark web has some legitimate uses, it is perhaps the most lenient of the three, with a mix of illegal activities carried out here. With anonymity as its hallmark characteristic, this web provides a soft landing place for criminal enterprises.


Illegal Markets
The best-known category of the this web are probably its marketplaces, in which illegal commodities and services are bought or sold. Most of these markets specialize in drugs, weapons, counterfeit currency, credit card information stolen on hacked computers, and almost anything else that someone could think to buy. The most well-known example probably has to be Silk Road, this web marketplace the FBI shut down in 2013.
Cybercrime Services
Moreover, there exist dark web service providers which are themselves cyber criminals making their services available. They include services such as hacking-for hire, malware sales to DDoS launching tools among other services. Most of them sell at a cryptocurrency called Bitcoin, which further adds to anonymity.
Human Trafficking and Exploitation
Sadly, dark web has also been used for even worse criminal activities, such as human trafficking, child exploitation, and trading in illegal content. Even though law enforcement agencies have had some level of success in closing down some of these operations. The anonymity of this makes it impossible to totally eradicate such activities.
Risks of Accessing the Dark Web
However, with anonymity comes significant threats, especially to inexperienced users.


Scams and Fraud
Scams abound on the dark web. Transactions are frequently affected through untraceable cryptocurrencies, so no court can recover lost funds for buyers or sellers if they are cheated. In this web, marketplaces frequently shut down overnight, leaving nothing behind, and taking money from the users with them.
Malware and Viruses
It also hosts malware and other viruses. When such malware is installed in one’s computer, then continues to visit untrustworthy sites or download files from unknown sources. Then one’s computer will eventually get infected. Another bad actor type is people who will create fake sites in the this masquerading. As legitimate services, steal user credentials, or infect their devices.
Law Consequences
Visiting the dark web is not illegal in any country, but if you find yourself engaging in illegal activities there, it will cost you in some serious legal terms. Every law enforcement agency around the world is watching out for illegal activity on the this. You can literally do absolutely nothing illegal, yet just by going to some of these websites, you can be a suspect.
Law Enforcement and the Dark Web
Even though this hides criminals’ identities, law enforcement has developed sophisticated ways of finding and processing them.


Operation Onymous
Operation Onymous is the coordinated effort of Europol, the FBI, and other law enforcement agencies. That in 2014 successfully removed several of the dark web’s most notorious marketplaces. In addition to arresting a large number of people associated with them.
How Law Enforcement Tracks Users
The police utilize several methods in tracing this web users. These include the securing of flaws in the Tor network, setting up honeypots. Which are decoy sites built to capture user details besides any other accessible information they can gather on cryptocurrency transactions. Despite all these efforts, some bad guys remain undetected in this web.
Challenges of Policing the Dark Web
It is pretty challenging to trace activities and identities because these sites use encryption, cryptocurrencies, and anonymization technologies. In addition, this providers may host their sites in countries with less strict legal systems. Because this is a global world of the internet; this complicates the whole shutdown process.
How to Access the Dark Web Safely
If you are interested in learning more about this and how to access it. The following are the safeguards you will need to use for secure conduct and anonymous operations.
Use a VPN
Before accessing this, be sure you use a Virtual Private Network. A Virtual Private Network encrypts your internet and hides your IP address, which adds even more security while navigating the this web.
Downloading Tor Browser
To access this web, you will need to download the Tor browser. Tor is a free browser and it allows for anonymous browsing. It is the tool most commonly used by people to get to .onion sites. Only download your Tor browser from the official website to avoid malware getting on it.
Stay Away from Illegal Activities
Consider the dark web only if you want to, and avoid any illegal activity. Apparently harmless activities, like visiting certain websites, can trigger the attention of law enforcement. Don’t shop, either, as many markets have some pretty shady elements at play.
Conclusion
The dark web is a complicated and controversial Internet part. It is so interesting because it contains tools that have helped individuals to maintain their privacy, freedom of speech, and ensure secrecy in communication. Conversely, it thrives with illicit markets and cybercrime, which can prove lethal. Whether you access this web for legitimate reason or out of pure curiosity, you should be aware of the risks involved and take precautions against its risks. Knowing this works and even different dangers. That lurk in the it is the best way to make decisions of whether this hidden world is worth diving into. In short, this web is the true mirror of humanity’s best and worst.
